Editor’s note: this story is paired with “Industry tips for securing online information”
Suddenly, it’s gone. All of it. All of the computer’s files, documents and stored information have vanished in an instant.
Then, a message appears. For a few hundred dollars, all of those lost files could be restored. But, now another dilemma arises. Is there any guarantee that the person on the other end of the line will stick to their word?
The preceding example describes a ransomware attack, just one of the many tools in an already impressive hacker arsenal. Attacks like these and many others have compromised the information of both average people and massive corporations like Equifax, whose recent data breaches exposed the personal information of an estimated 145 million Americans as of early October.
Working against these hackers are a variety of cybersecurity companies who make up an industry that is projected to be worth $120 billion. In fact, it is estimated that nearly $1 trillion dollars will be spent on cybersecurity services or products over the next five years, according to Cybersecurity Ventures, a researcher and publisher that specializes in covering the global cyber economy.
However, the biggest threats facing this multi-billion-dollar industry do not seem to stem from fancy code or malware, but rather from exploiting human error through social engineering and clever phishing schemes.
“You have to ask yourself, ‘What creates incentives for bad guys?’” said Proofpoint Senior Vice President and General Manager Darren Lee. “You have hackers now thinking ‘let’s not target the system; let’s target a person.’”
With advances in cybersecurity technology, companies are now able to roll out patches and corrections to programs relatively quickly, “but you can’t patch a human,” said Lee.
Instead, hackers have begun targeting individual users through a process known as social engineering. Social engineering uses a combination of psychological manipulation and confidence scams to to acquire personal information, like passwords, birth dates or other identifying factors, which then allows hackers to access even more sensitive information.
The most efficient way for hackers to acquire information is to directly target primary points of communication like email or social media.
“These socially engineered attacks are dramatically on the rise and are increasing in sophistication,” said Lee. “They are really quite clever in many cases in how they will talk a respondent into taking action that creates a problem.”
An example of this action that Lee provided was a fraudulent email that is designed to appear like a correspondence between top level executives asking for important financial information. The employee receiving this email assumes it to be legitimate and sends the requested data to what is actually a clever hacker using social engineering to steal company information. The hacker is then free to sell or leverage that data in an attempt to get even more money.
Hackers can gather information through these social engineering techniques to also obtain credentials or password information that would allow them to then access other information like an individual’s personal files, or they can use individual employee login information to access a company’s database.
“With the privileged credentials to get into data, the next step is initiating a download,” said Lee. “You would rip that data right out of a database and can copy social security numbers or even the database itself. Once things are free and clear on my system, you can sell the data or use it for any other intent.”
Losing records in a breach can mean huge financial losses for a company that can stem from something as simple as confirming login information on what appears to be a social media site or email server.
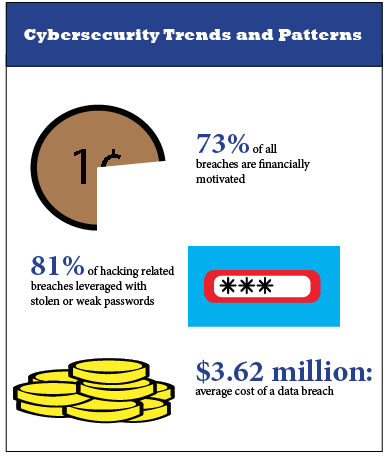
The Ponemon Institute’s 2017 Cost of Data Breach Study found that “the more records lost, the higher the cost of the data breach.” The cost for companies that lost less than 10,000 records was around $1.9 million and around $6.3 million for incidents with more than 50,0000 compromised records.
For a company like Equifax that lost well over 100 million records, the actual costs are insurmountable. Equifax’s CEO has already ‘retired’ in light of the breach, and between class-action law suits and recovery efforts, Equifax will most likely be paying for simple human error for years to come.
Cybersecurity is an industry where prevention provides the brightest hope for avoiding a breach. Once information is compromised, it can be incredibly difficult for victims of cybercrime to recover.
For personal users, Lee suggested keeping backups of all data. Using a terabyte hard drive or uploading data through a secure cloud connection can offer an alternative in the face of ransomware attacks, where data is stolen from a computer.
But more than just backups, the most important thing is simply being aware, said Lee.
For more information concerning the cybersecurity industry or trends from the past year, consult the Verizon 2017 Data Breach Investigations Report or the Ponemon Institute 2017 Cost of Data Breach Study.




