Editor’s note: this story pairs with “Human error increasingly responsible for online data breaches”
It is estimated there will be nearly 4 billion online users and over 300 billion passwords in use by 2020, according to HEROIC Cybersecurity, a cybersecurity firm that offers services to both individuals and large-scale enterprises.
With this increase in online users has come an increase in cybercrime. The Wall Street Journal estimated that cybercrime cost users and companies around $100 billion in 2013. That number has tripled in the past few years, according to data compiled by Forbes.
While many cybersecurity companies offer services to larger corporations, there is now a need for individuals to protect their own data. Hackers are relying more on social engineering and exploiting human error. It is vital to take measures to make sure personal data does not end up stolen and sold online.
Professionals within the cybersecurity industry have proposed the following suggestions for safeguarding personal data online:
Entering Information
Social engineering (which relies on human interaction and tricking users into giving away information) has become more popular than conventional malware attacks. Users should be cautious any time they have to enter information online, said Proofpoint Senior Vice President and General Manager Darren Lee.
Hackers will create pages that mimic popular outlets like Gmail or Facebook and trick users into entering their username and password. Check the spelling of URLs and anything else that appears out of place before entering sensitive information.
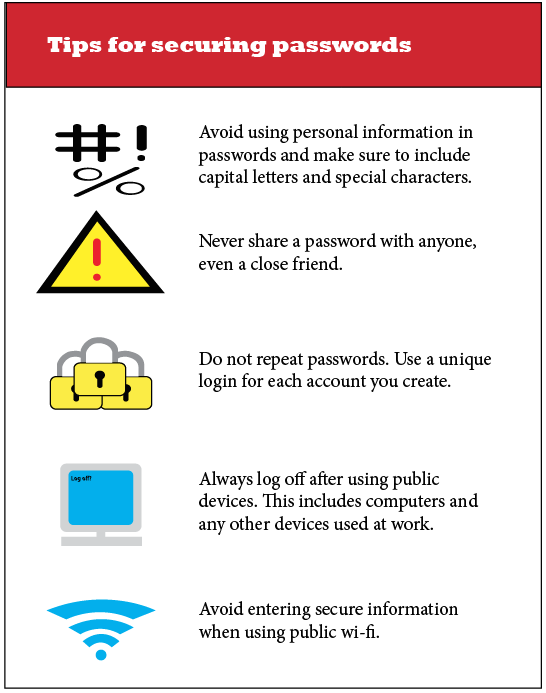
Password Protection
Many people will lose their information as the result of human error as opposed to sophisticated programming. Losing a password this way can be devastating, as many people use the same login information across all of their online accounts.
“The data shows that the good majority of people have over 40 online accounts which means they should make 40 passwords and they each need to be unique and they each need to be strong,” said Heroic Cybersecurity Public Relations Manager Wyatt Semanek.
Unique passwords take time and effort to set up and track, but they will keep someone from accessing all of a user’s information across multiple platforms with just a single set of login credentials.
Recognizing Card Skimmers
Card skimmers are devices that are fitted into ATMs or other devices that read credit cards. The skimmer can read the magnetic strip of a credit card and then store that information until someone retrieves the skimmer and downloads the data.
These devices have grown more common; the Verizon 2017 Data Breach Investigations Report states that the “installation of skimmers inside gas pump terminals and ATMs account for almost 60 percent of non-ecommerce retailer breaches.”
Despite this growing trend, there are now apps available that offer protection against card skimming technology and can detect the frequencies used by these devices. More information about these apps can be found here.
Combating Ransomware
Ransomware refers to a technique where a hacker will steal the personal information of an individual and hold it hostage until a specific payment is made. It may seem like the only solution is to pay the ransom, but there is no guarantee that a hacker will cooperate once a payment is made.
Each ransomware case is unique and users should immediately contact law enforcement if their information is ever compromised in this way. For the FBI’s recommendations for combating ransomware, click here.
Two-Factor Authentication
Two-factor authentication, a service now required for anyone with a BYU Net ID, adds another layer of security when attempting to access secure information. Whenever a user tries to log on to a specific site or database, two-factor authentication requires the user to confirm their identity through a second means like a fingerprint, identifying information, or more commonly, through another device like a phone or tablet. Once authentication occurs through the second confirmation, the user can then access their secure information. Measures like this are an additional protection and safeguard information in the case a password or login information is lost.




